Setting a minimum TLS version with CloudFlare
How to set a minimum TLS version on CloudFlare and why you should consider it
Back in the day, the typical way to secure your website was to purchase an SSL certificate, install it, and make sure all your traffic was using https and not http. Job done, right?
Not quite.
The underlying principles that guided the certificates have improved over time, getting more secure. These days we don’t even talk about SSL anymore; it is TLS. TLS (Transport Layer Security) is the successor to SSL and is the defacto security protocol for the web.
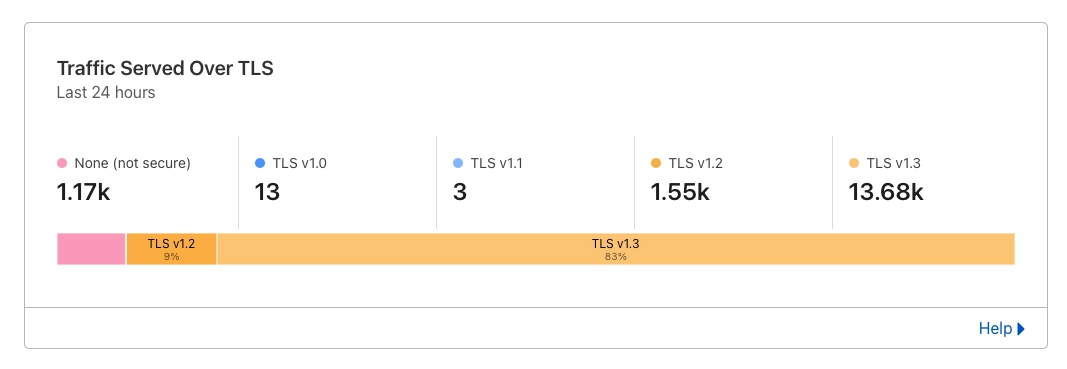
It has gone through several versions, from 1.0, 1.1, 1.2, and we’re currently on 1.3.
The older versions of TLS (1.0 and 1.1) are not secure anymore. The right types of attack render them useless.
This means that even if your website has HTTPS enabled and your server accepts TLS 1.3, if it also accepts TLS 1.0, then a browser or API request that uses TLS 1.0 could be exposed to attack.
How we fix this is by only allowing specific versions of TLS to be allowed by your server.
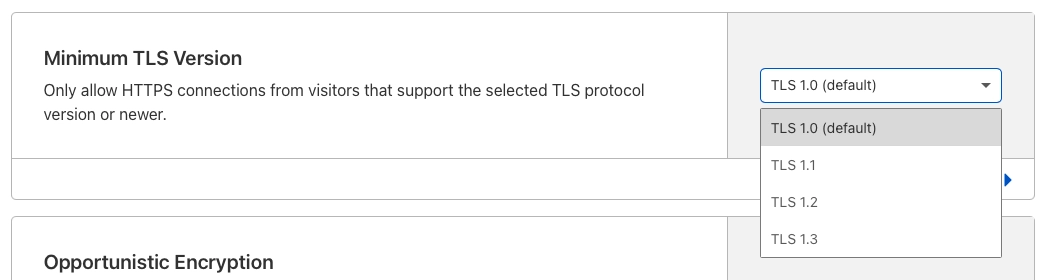
If you’re using CloudFlare to manage your DNS and certificates, limiting the version of TLS used is just a few clicks away.
- From your dashboard, select the SSL/TLS icon
- Click the “Edge Certificates” subsection
- Under “Minimum TLS Version”, select the minimum version you want to allow
Here are some screenshots to help.

Should I always set a higher minimum version?
CloudFlare defaults to accepting everything, and you’d think they know best, right?
It depends on what you’re protecting and who you need to support.
Reasons why you might keep a TLS 1.0 around;
- You need to support users who have ancient browsers who cannot do anything better than TLS 1.0
- You have a third party system making calls that can only accept/send stuff over TLS 1.0
- You only use HTTPS because that is what the cool kids use, and you’re hosting a static website with nothing to protect
Reasons why you might tune your setting only to allow newer TLS versions (1.2 and above);
- You need your communication to be secure
- You want to dissuade bots/bad actors who are using older implementations on purpose
The nice thing about using CloudFlare is if you make the change, you can always change it back if you spot issues.
If you aren’t sure how much traffic you are serving over the different TLS versions, you can check CloudFlare for a 24-hour view. This can be found in your main SSL/TLS overview.